BitLocker Drive Encryption technology helps protect data on your local and external drives by encrypting the contents of logical volumes. In this article, we’ll have a look at two ways to extract data from a BitLocker-encrypted partition. The first involves decrypting the BitLocker-protected partition using the standard Windows tools. The second way suggests that the file system of the encrypted drive is corrupted (the area of the drive where BitLocker stores its metadata is damaged) or that Windows won’t boot.
Requirements for data recovery from a BitLocker volume
In order to recover data from a drive that is encrypted with BitLocker, you would need to have at least one of the BitLocker protection elements:
- BitLocker password (the one that you enter in the Windows GUI to unlock the encrypted drive);
- The BitLocker Recovery key;
- System startup key (.bek) – a key file on a USB flash drive that allows you to automatically decrypt the boot partition without requiring the user to enter a password.
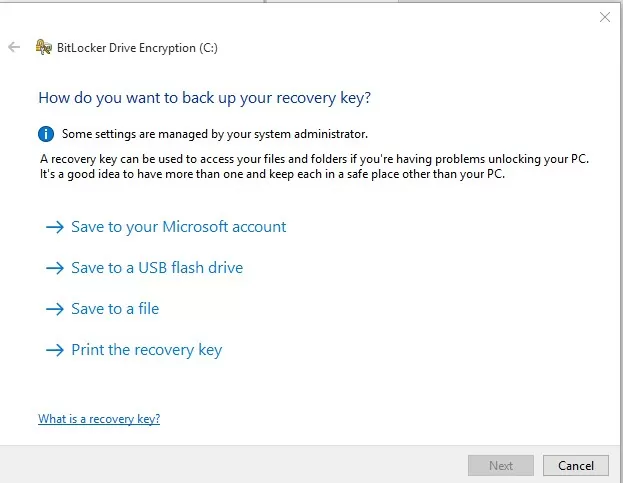
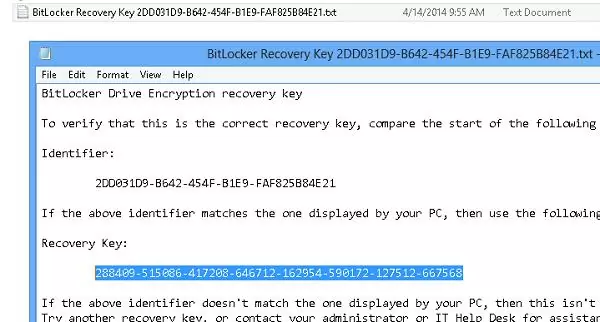
The BitLocker recovery key is a unique sequence of 48 characters. The recovery key is generated before Bitlocker starts the partition encrypton. You can print the recovery key, save it as a text file on external media, or save it to your Microsoft account.
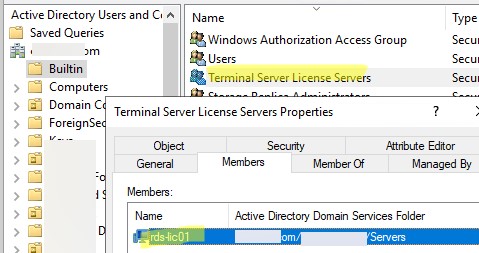
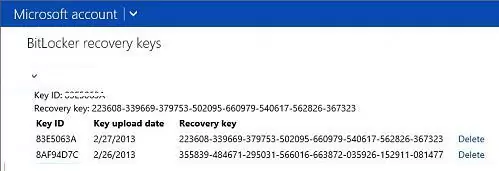
You can find the Bitlocker recovery key in your account on the Microsoft website https://onedrive.live.com/recoverykey.
For computers that are joined to an Active Directory domain, an administrator can configure GPOs to automatically save BitLocker recovery keys in the computer’s account attribute in AD.
If you do not have a recovery key, you will not be able to access your data.
How to Unlock a BitLocker Encrypted Drive in Windows?
The easiest way to unlock a BitLocker-encrypted drive is from the Windows GUI.
Connect the drive to your computer and go to the Control Panel -> System and Security -> BitLocker Drive Encryption (available in Professional and Enterprise Windows editions). Select the BitLocker-encrypted disc and click Unlock Drive.
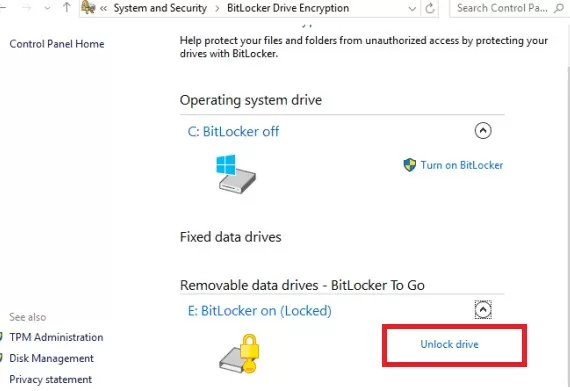
It is not possible to encrypt or decrypt a BitLocker volume on a computer that is running Windows Home Edition.
Depending on the security method, specify the password, PIN, or connect the smart card to unlock the drive. If you don’t know the password, you can use the recovery key to decrypt the volume. Select Advanced settings -> Enter recovery key.
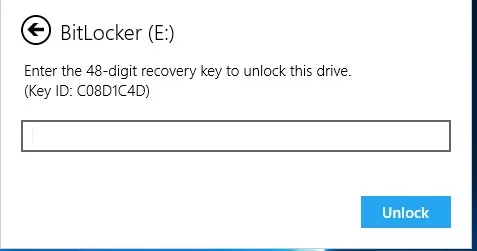
If you have more than one recovery key, you can identify the one you need by the Key ID part displayed in the prompt window. If you have entered the correct key, the drive will be unlocked and you will be able to access files on the BitLocker drive.
You can also use PowerShell to disable BitLocker protection for a specific volume:
Disable-BitLocker -MountPoint "C:"
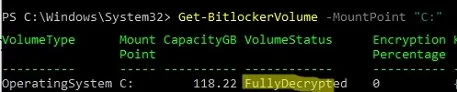
Wait for partition decryption to be complete. Check that the drive has been decrypted:
Get-BitlockerVolume -MountPoint "C:"
VolumeStatus: FullyDecrypted
Disable BitLocker Encryption for System Drive in Windows Recovery Environment
If your system drive is encrypted by BitLocker and Windows no longer boots (due to incorrect updates, Blue screen of death, freezes on startup, etc.), you can use Windows Recovery Environment (Windows RE) to decrypt the drive.
The WinRE recovery environment should start automatically if Windows fails to boot 3 times in a row. You can also boot your computer from any Windows installation USB flash drive, MS DaRT recovery image, or other LiveCD. If you are using a Windows installation media, press Shift+F10 at the language selection stage (or in WinRE select Troubleshoot -> Advanced options -> Command Prompt).
The WinPE command prompt should appear.
You need to find a Bitlocker encrypted drive letter. To check the status of all available drives in WinPE, run:
manage-bde -status
The result of the command for one (or several) of the drives should contain the following text: “BitLocker Drive Encryption: Volume D”. So you have disk D encrypted.
Unlock the drive by running the command:
manage-bde -unlock D: -pw
The command prompts for a BitLocker password:
Enter the password to unlock this volume:
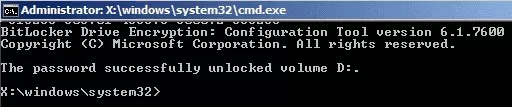
If the password is correct, a message will appear:
The password successfully unlocked volume D:.<p/re>
If you don’t know the BitLocker password, you can use the recovery key to unlock the volume:
manage-bde -unlock D: -RecoveryKey J:\1234567...987ABCDE4564.bek
Your drive is unlocked and you can start repairing the Windows boot loader or fixing other problems.
To unlock the drive and disable BitLocker drive protection altogether, run:
manage-bde -protectors -disable D:
Restart your computer. The drive is now unencrypted.
Using BitLocker Repair Tool (Repair-bde) to Recover Encrypted Drive
To recover data from a damaged/inaccessible BitLocker volume, you must use the Repair-bde (BitLocker Repair Tool) console tool.
Try to decrypt and extract the data to a new drive using the BitLocker password. The repair-bde utility allows you to restore data from a damaged volume to a new partition. Note that the target partition must be larger than the source BitLocker volume and that existing data on the target volume will be deleted (!).
- Open the command prompt as an administrator;
- Run the following command:
repair-bde D: F: -pw –Force, where D: is a disk with the BitLocker data, and E: is an empty drive (partition) to extract the decrypted data to; - Specify the Bitlocker Password (used by the user to unlock the encrypted volume using the Windows GUI).
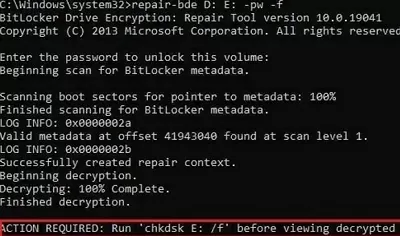
The repair-bde utility will attempt to recover critical metadata from your encrypted volume and use it for decryption.
If the data has been successfully decrypted, the following message will appear:
Decrypting: 100 completed
Finished decryption.
ACTION REQUIRED: run chkdsk E: /f before viewing decrypted data
You can use the recovery key or the system boot key to decrypt the volume if you don’t know the BitLocker password (if the system partition is encrypted).
Use a Recovery Key to start recovering data from the BitLocker partition:
repair-bde D: E: -rp 288209-513086-417508-646412-162954-590672-167552-664563 –Force
If BitLocker is used to encrypt the Windows system partition and a special boot key on a USB flash drive is used to boot the operating system, you can decrypt the volume as follows:
repair-bde D: E: -rk I:\2F538474-923D-4330-4549-61C32BA53345.BEK –Force
where 2F538474-923D-4330-4549-61C32BA53345.BEK s the BitLocker drive encryption startup key on the USB flash drive I: (this file is hidden by default).
After unlocking the volume, you need to check the target drive using the command:
Chkdsk E: /f
Note. If you have failed to recover data from an encrypted drive using the above methods, you should try making a sector-by-sector copy of the damaged partition using the DDRescue Linux tool (or another similar utility for recovering data from damaged partitions). Then try to recover the data from the resultant copy in accordance with the scenario described.
You can also open a BitLocker-encrypted drive from Linux. To do this, you will need the DisLocker tool and a BitLocker recovery password or key.
Use your package manager to install the tool. If you are running Ubuntu/Debian, use the command:
$ sudo apt-get install dislocker
Go into the mnt directory and create two directories (one for the encrypted partition and one for the decrypted one):
$ cd /mnt
$ mkdir encrypted
$ mkdir decrypted
Locate the encrypted partition (fdisk -l command) and decrypt it using the BitLocker password:
$ sudo dislocker -V /dev/sdb1 -u -- /mnt/encrypted
If you have a recovery key, use this command:
$ sudo dislocker -r -V /dev/sdb1 -p your_bitlocker_recovery_key /mnt/encrypted
The DisLocker utility uses the Filesystem in Userspace (FUSE) driver to access an encrypted partition in read-only mode.
The dislocker-file will appear in the target directory. This file contains your NTFS data partition.
To see all the files on the unencrypted partition, you can mount it:
$ sudo mount -o loop /mnt/encrypted/dislocker-file /mnt/decrypted